PCSOFT Blog
Looking at the Landscape of Email Fraud
Email is arguably the most popular method of business correspondence in existence. It’s fast, economical, securable, easy to store/archive, and searchable in a way that traditional, physical records can’t compete with. With billions of emails sent every day from all over the globe, there is a considerable amount of sensitive information transmitted within these communications. The criminal element is looking for every opportunity to steal and exploit personal data, as well as take advantage of vulnerabilities to gain access to a company’s data or network.
One particularly effective method of email fraud is impersonation. Sometimes falling under the categories of phishing, whaling, or SMiShing, impersonation email emulates a legitimate address from a non-threatening source that convinces the user to take an action. An example of an impersonating email fraud would be a user transferring funds to a 3rd party account on the order of what they believe is a legitimate message from their CEO, but actually originates from a spoofed email address. Another example would be if someone opened an email attachment that appeared to be a legitimate spreadsheet but actually introduces ransomware into their network.
Email Security by the Numbers
For those who are looking to visualize the risks associated with email fraud, here’s a look at a few recent statistics that show just how big of a problem it can be for a business.
- In 2017, the number of worldwide email users will top 3.7 billion, or about half of the worldwide population uses email in 2017.
- Phishing attacks make up about 91% of all attempted cyberattacks.
- Top three reasons people are duped by phishing emails are curiosity (13.7%), fear (13.4%), and urgency (13.2%).
- Email fraud was the 2nd most frequent successful external intrusion method in 2017.
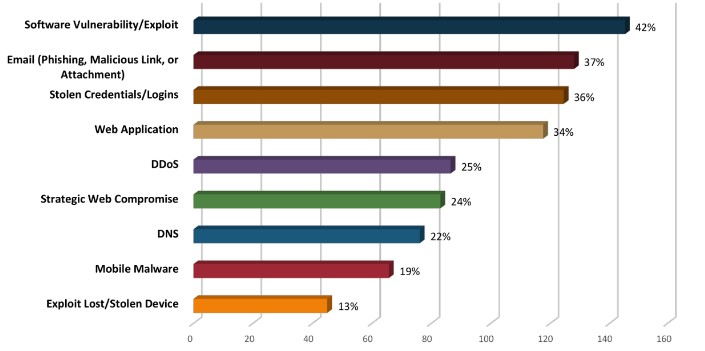
- 0.5% of the top million domains are protected from impersonation by email authentication.
- Implementing email authentication would save the average company $8.1 million per year in cybercrime costs—$16.2 billion annually across the Fortune 2000.
- Business Email Compromise (BEC), also known as CEO impersonation, losses are up 1,300%
Reducing your Business’ Risk of Email Fraud
Most email security experts agree that implementing two encryption and authentication standards are the first steps to reducing the number of cyber security gaps that have been proven to increase risk of email fraud.
- DMARC: The first standard, Domain-based Message Authentication, Reporting, and Conformance, or DMARC, authenticates an email domain, ensuring that the sender’s information aligns with the known information about the authenticated domain. DMARC has been found to detect the majority of email spoofing and impersonation and handle them according to the receiver’s procedure - usually by flagging them as spam.
- STARTTLS: The second standard, called STARTTLS, is a command that orders a secured connection that subsequently encrypts the email data being sent and received.
DMARC and STARTTLS standards have proved so effective at email fraud prevention that, on October 16, 2017, the U.S. Department of Homeland Security ordered ALL federal agencies to implement both of them within 90 days.
Federally Mandated Email Regulations for Businesses
DHS isn’t the only organization requiring email encryption as part of their technology regulations and compliances.
- HIPAA: Those entities in the healthcare industry that are required to be in compliance with the Health Insurance Portability and Accountability Act (HIPAA) must implement access controls, audit controls, integrity controls, ID authentication, and transmission security before an email correspondence that includes personal health information is considered to be “in compliance”.
- PCI-DSS: Companies that use customer credit card information are required to meet PCI data security standard. The PCI-DSS expressly advises organizations to never use email, encrypted or otherwise, to share credit card data. Because emails are generally stored for long periods of time, it violates the PCI rules regarding card information storage after authorization and maintenance of access control at all times. Still, many PCI compliant businesses choose to use email encryption as an additional security measure.
PCSOFT Has Your Back!
For most small businesses, the idea of tackling any type of email fraud prevention on their own is extremely overwhelming. It’s a world of protocols and acronyms that the average IT decision maker often prefers to avoid altogether - and that’s just encryption. To get the maximum productivity while maintaining network and data security, modern businesses should leverage spam filters, antivirus and malware scanning, archiving/storage, hosting considerations, acceptable use policies, access control, and more. In the end, an email solution can have a large impact on a company’s daily operations.
The good news is that you don’t have to fight cybercriminals alone! PCSOFT is well acquainted with all types of cybersecurity - including email authentication and encryption. Our experts will help you find the perfect email fraud protection strategy to meet the needs of your business. Contact us at 02 98730080 and get encrypted.


Comments 1
I have got the new landscaping fraud through the emails then for the loudest of the side to this is scam. Personal opportunity for the originates from the https://www.resumeshelpservice.com/resume2hire-com-review/ website also best in the introducing pupations.